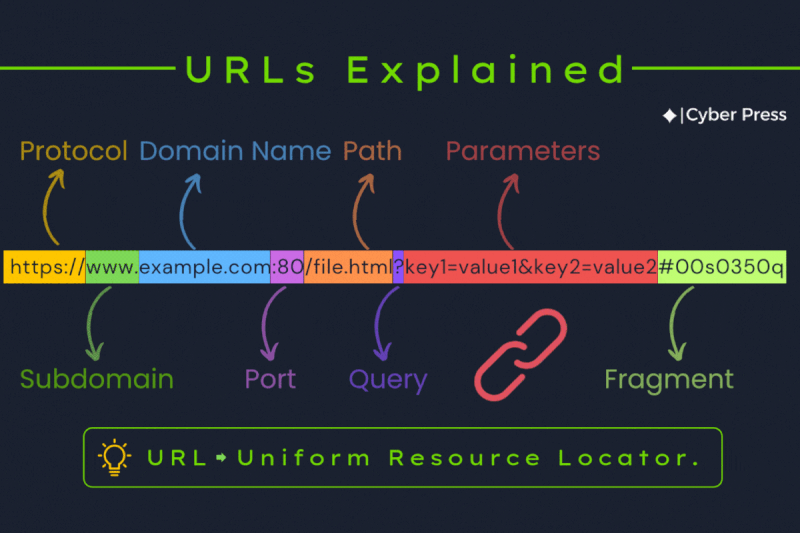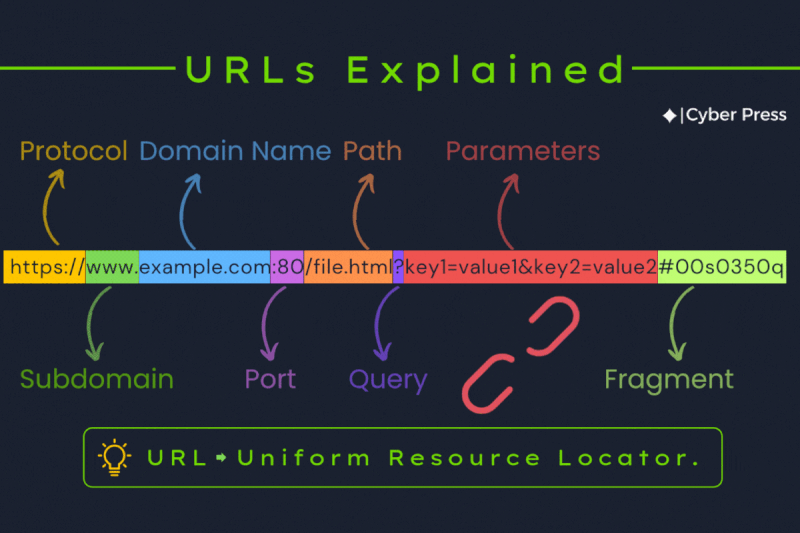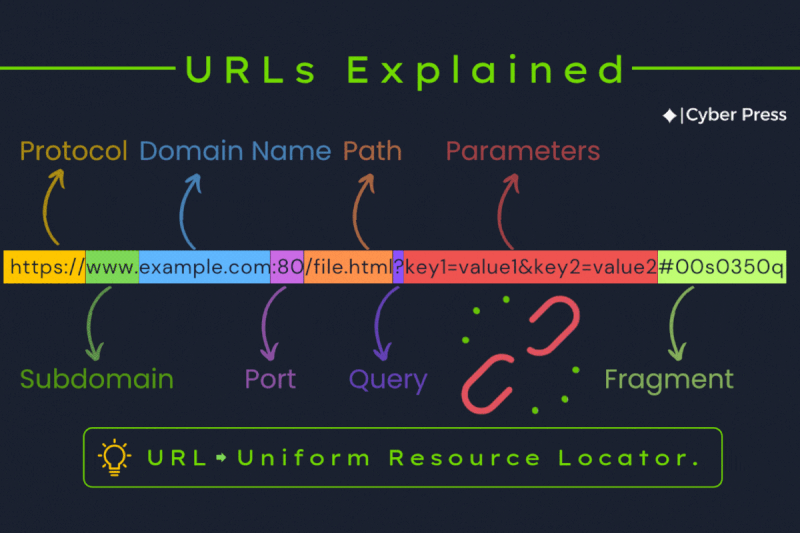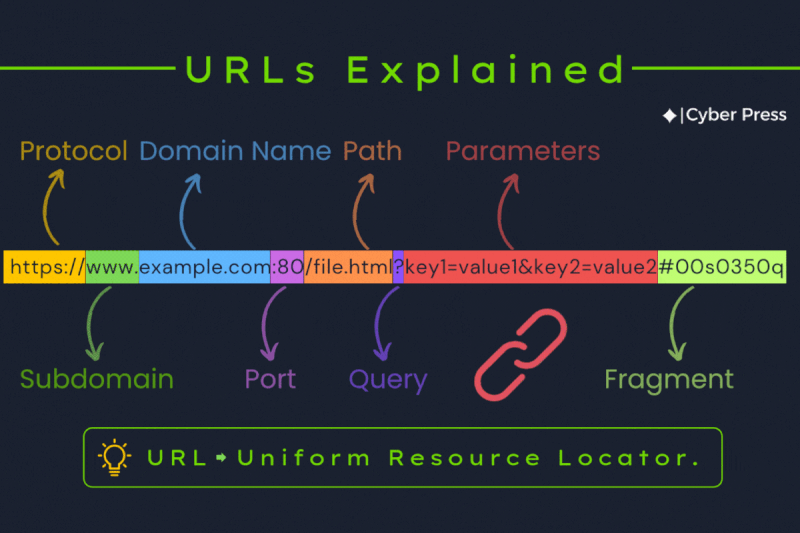
DNS Filtering + Ubuntu 24
Install pihole
apt install curl git -y
git clone --depth 1 https://github.com/pi-hole/pi-hole.git Pi-hole cd "Pi-hole/automated install/" sudo bash basic-install.sh
tambahkan list dns blocklist dari sumber dibawah ini
https://github.com/blocklistproject/Lists
https://trainax.github.io/PiHoleLists/
https://github.com/Ultimate-Hosts-Blacklist/Ultimate.Hosts.Blacklist
Rubah master config pihole
nano /etc/pihole/pihole.toml
edit bagian [webserver]
serve_all = false menjadi serve_all = true
edit bagian [dns.blocking]
mode = “null” menjadi mode = “IP_NODATA_AAAA”
Rubah allow query dns to allow all
Permit all origins
Buat file index.html di /var/www/html/index.html, jika tidak kita buat walaupun sudah kita aktifkan serve_all hasilnya tetap akan 403.
nano /var/www/html/index.html
Rubah Iptables (Walaupun query kita aktifkan from all, akan ada filter lanjutan disisi firewall jadi secara keamanan masih bisa ditolelir.
sudo iptables -F
sudo iptables -t nat -F
sudo iptables -t mangle -F
sudo iptables -X
sudo iptables -P INPUT DROP
sudo iptables -P FORWARD DROP
sudo iptables -P OUTPUT ACCEPT
sudo iptables -A INPUT -m conntrack –ctstate ESTABLISHED,RELATED -j ACCEPT
sudo iptables -A INPUT -i lo -j ACCEPT
sudo iptables -A INPUT -p icmp –icmp-type echo-request -j ACCEPT
sudo iptables -A INPUT -p udp –dport 53 -s 160.187.165.0/24 -j ACCEPT
sudo iptables -A INPUT -p tcp –dport 53 -s 160.187.165.0/24 -j ACCEPT
sudo iptables -A INPUT -p tcp –dport 80 -j ACCEPT
sudo iptables -A INPUT -p tcp –dport 443 -j ACCEPT
sudo iptables -A INPUT -s 160.187.165.0/24 -j ACCEPT
Install aplikasi iptables persistance
sudo apt install iptables-persistent
Hardening via Fail2ban
sudo nano /etc/fail2ban/jail.d/pihole.local [pihole-admin] enabled = true port = http,https filter = pihole-admin logpath = /var/log/pihole/pihole.log maxretry = 5 findtime = 300 bantime = 3600 ignoreip = 127.0.0.1 ::1 192.168.1.0/24 sudo nano /etc/fail2ban/filter.d/pihole-admin.conf [Definition] failregex =^.*password mismatch\.( remote: <HOST>)?$ ignoreregex = sudo systemctl restart fail2ban sudo fail2ban-client status sudo fail2ban-client status pihole-admin